Playing around with podman and setting up rootless containers in Arch
Category: en
These days I have been playing around with a different set of technologies in my side projects, and I stumbled across a different containerization engine called podman.
It is a container engine very similar to and compatible with the current defacto tool in containerization space, Docker. Podman is from Red Hat and it’s sort of like a replacement for Docker because it uses the same syntax, same command, and even got tools like podman-docker to emulate docker CLI in podman.
However, there are a few keys underlying differences between Podman and Docker
- Docker uses a daemon which is a program running in the background to handle services and processes. Unlike docker, podman is daemonless. You can read more about what is docker daemon here. Running daemonless means, it runs containers under the user starting the container.
- Podman runs the container in rootless mode. This is considered to be safer than containers with root privileges. IIRC, docker also added rootless mode, you can check it here.
Podman is also more towards modularity compared to docker. For example, docker can build images on its own, however, in podman it uses another tool called Buildah to build images. Calling podman build will actually calls buildah bud behind the scene.
Since podman is a drop-in, you can use docker-compose with podman as well, or instead, you can use podman-compose which also works just like docker-compose.
Rootless containers in Arch
Running rootless in Arch is a bit tricky because in Arch subordinate user ids and subordinate group ids does not exist. These contain a list of users and user ids that the user is allowed to impersonate.
If you have not created those two files, you will receive an error as below.
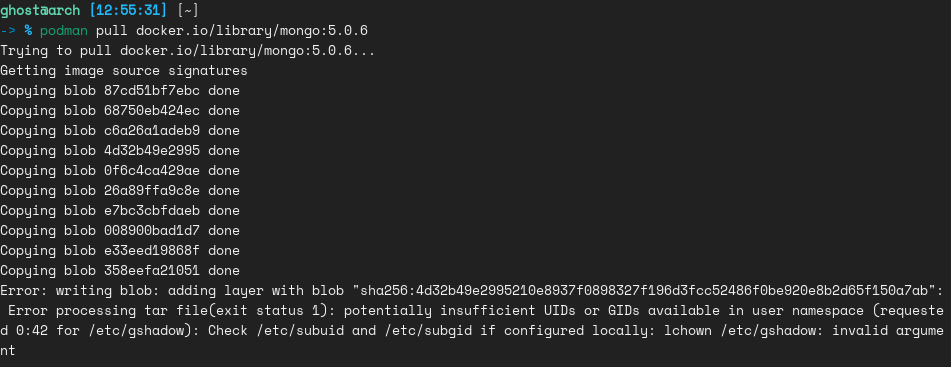
Podman requires the user running the rootless container to have a range of UIDs listed in those files. Here is an explanation of how does Podman rootless works, and feel free to read about there for a better explanation of how it is working in underlying.
So first create files as below in root shell
touch /etc/subuid
touch /etc/subgid
run the following command to assign a range of subordinate users and groups to username
usermod --add-subuids 100000-150000 --add-subgids 100000-150000 username
Finalise the changes as below in user shell
podman system migrate

